|
|
| (4 intermediate revisions by the same user not shown) |
| Line 7: |
Line 7: |
| == Big Ideas in Databases == | | == Big Ideas in Databases == |
|
| |
|
| * [[Data modeling]]
| |
| * [[Entity relationship diagramming]] | | * [[Entity relationship diagramming]] |
| * Entity relationships
| |
| * Working with entity relationships
| |
| * [[Normalization]] | | * [[Normalization]] |
| * [[Unique identifiers]]
| |
| * Transforming From Conceptual Model to Physical Model
| |
| * Introduction to SQL
| |
| * SELECT Statements and Relational Database Technology
| |
| * Using the WHERE Clause
| |
| * Restricting Rows and Introduction to Functions
| |
| * Using Character, Number, and Date Functions
| |
| * Using Single Row Functions
| |
| * Fundamentals of Database Security
| |
| * Understanding Database Transactions
| |
| * MySQL: monitoring and performance
| |
| * MySQL: security
| |
| * [[ACID]]
| |
| * [[CRUD]]
| |
| * [[NoSQL]] (Advanced)
| |
|
| |
|
|
| |
|
| == Standards == | | == ACID == |
|
| |
|
| These standards are taken from the IB Computer Science database option. <ref>IB Diploma Program Computer science guide (first examinations 2014). Cardiff, Wales, United Kingdom: International Baccalaureate Organization. January 2012.</ref>
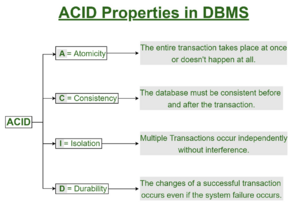
| | In computer science, ACID (atomicity, consistency, isolation, durability) is a set of properties of database transactions intended to guarantee data validity despite errors, power failures, and other mishaps. In the context of databases, a sequence of database operations that satisfies the ACID properties (which can be perceived as a single logical operation on the data) is called a transaction. For example, a transfer of funds from one bank account to another, even involving multiple changes such as debiting one account and crediting another, is a single transaction.<ref>https://en.wikipedia.org/wiki/ACID</ref> |
|
| |
|
|
| |
|
| * Discuss the need for databases.
| | [[File:Acid.png|thumb]] |
| * Outline the differences between data and information.
| |
| * Outline the differences between an information system and a database.
| |
| * Describe the use of transactions, states and updates to maintain data consistency (and integrity).
| |
| * Define the term database transaction.
| |
| * Explain concurrency in a data sharing situation.
| |
| * Explain the importance of the ACID properties of a database transaction.
| |
| * Describe the two functions databases require to be performed on them.
| |
| * Explain the role of data validation and data verification.
| |
| * Explain data modeling
| |
| * Apply understanding of entity relationship diagramming
| |
| * Define entity relationships
| |
| * Use unique identifiers and normalization
| |
| | |
| * Define the terms: database management system (DBMS) and relational database management system (RDBMS).
| |
| * Outline the functions and tools of a DBMS.
| |
| * Describe how a DBMS can be used to promote data security.
| |
| * Define the term schema.
| |
| * Identify the characteristics of the three levels of the schema: conceptual, logical, physical.
| |
| * Outline the nature of the data dictionary.
| |
| * Explain the importance of a data definition language in implementing a data model.
| |
| * Explain the importance of data modelling in the design of a database.
| |
| | |
| * Define the following database terms: table, record, field, primary key, secondary key, foreign key, candidate key, composite primary key, join.
| |
| * Identify the different types of relationships within databases: one-to- one, one-to-many, many-to-many.
| |
| * Outline the issues caused by redundant data.
| |
| * Outline the importance of referential integrity in a normalized database.
| |
| * Describe the differences between 1st Normal Form (1NF), 2nd Normal Form (2NF) and 3rd Normal Form (3NF).
| |
| * Describe the characteristics of a normalized database.
| |
| * Evaluate the appropriateness of the different data types.
| |
| | |
| * Construct an entity-relationship diagram (ERD) for a given scenario.
| |
| * Construct a relational database to 3NF using objects such as tables, queries, forms, reports and macros.
| |
| * Explain how a query can provide a view of a database.
| |
| * Describe the difference between a simple and complex query.
| |
| * Outline the different methods that can be used to construct a query.
| |
| | |
| * Explain the role of a database administrator.
| |
| * Explain how end-users can interact with a database.
| |
| * Describe different methods of database recovery.
| |
| * Outline how integrated database systems function.
| |
| * Outline the use of databases in areas such as stock control, police records, health records, employee data.
| |
| * Suggest methods to ensure the privacy of the personal data and the responsibility of those holding personal data not to sell or divulge it in any way.
| |
| | |
| * Discuss the need for some databases to be open to interrogation by other parties (police, government, etc).
| |
| * Explain the difference between data matching and data mining.
| |
| | |
| * Describe the characteristics of different database models.
| |
| * Evaluate the use of object-oriented databases as opposed to relational databases.
| |
| * Define the term data warehouse.
| |
| * Describe a range of situations suitable for data warehousing.
| |
| * Explain why data warehousing is time dependent.
| |
| * Describe how data in a warehouse is updated in real time.
| |
| * Describe the advantages of using data warehousing.
| |
| | |
| * Explain the need for ETL processes in data warehousing.
| |
| * Describe how ETL processes can be used to clean up data for a data warehouse.
| |
| * Compare the different forms of discovering patterns using data mining.
| |
| * Describe situations that benefit from data mining.
| |
| * Describe how predictive modelling is used.
| |
| * Explain the nature of database segmentation.
| |
| * Explain the nature and purpose of link analysis.
| |
| | |
| * Describe the process of deviation detection.
| |
|
| |
|
| == See also == | | == See also == |