Hashing: Difference between revisions
Mr. MacKenty (talk | contribs) No edit summary |
Mr. MacKenty (talk | contribs) |
||
| (10 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
[[file:computation.png|right|frame| | [[file:computation.png|right|frame|Advanced programming<ref>http://www.flaticon.com/</ref>]] | ||
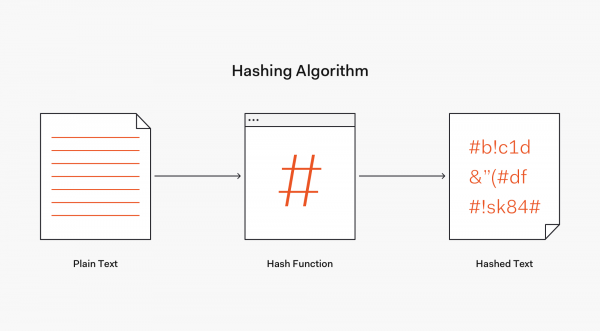
A hash function is any function that can be used to map data of arbitrary size to fixed-size values. The values returned by a hash function are called hash values, hash codes, digests, or simply hashes. The values are used to index a fixed-size table called a hash table. Use of a hash function to index a hash table is called hashing or scatter storage addressing.<ref>https://en.wikipedia.org/wiki/Hash_function</ref> | A hash function is any function that can be used to map data of arbitrary size to fixed-size values. The values returned by a hash function are called hash values, hash codes, digests, or simply hashes. The values are used to index a fixed-size table called a hash table. Use of a hash function to index a hash table is called hashing or scatter storage addressing.<ref>https://en.wikipedia.org/wiki/Hash_function</ref> | ||
| Line 5: | Line 5: | ||
Hashing is the transformation of a string of characters into a usually shorter fixed-length value or key that represents the original string. Hashing is used to index and retrieve items in a database because it is faster to find the item using the shorter hashed key than to find it using the original value. It is also used in many encryption algorithms.<ref>https://searchsqlserver.techtarget.com/definition/hashing</ref> | Hashing is the transformation of a string of characters into a usually shorter fixed-length value or key that represents the original string. Hashing is used to index and retrieve items in a database because it is faster to find the item using the shorter hashed key than to find it using the original value. It is also used in many encryption algorithms.<ref>https://searchsqlserver.techtarget.com/definition/hashing</ref> | ||
[[File:Hashing.png] | [[File:Hashing.png|600px]] | ||
== Benefit of hashing == | |||
One main use of hashing is to compare two files for equality. Without opening two document files to compare them word-for-word, the calculated hash values of these files will allow the owner to know immediately if they are different. | |||
Hashing is also used to verify the integrity of a file after it has been transferred from one place to another, typically in a file backup program. To ensure the transferred file is not corrupted, a user can compare the hash value of both files. If they are the same, then the transferred file is an identical copy. | |||
In some situations, an encrypted file may be designed to never change the file size nor the last modification date and time (for example, virtual drive container files). In such cases, it would be impossible to tell at a glance if two similar files are different or not, but the hash values would easily tell these files apart if they are different.<ref>https://www.2brightsparks.com/resources/articles/introduction-to-hashing-and-its-uses.html</ref> | |||
== Simple Code sample == | |||
<syntaxhighlight lang="python"> | |||
# this python file should be used as part of your process to understand hashing. | |||
# please change values so you can see how hashing works! | |||
import hashlib | |||
string = "hello there." | |||
print(string) | |||
hashed_string = hashlib.sha256(string.encode()).hexdigest() | |||
print(hashed_string) | |||
# Thank you to Max S for coming up with this sample | |||
</syntaxhighlight> | |||
== Videos == | == Videos == | ||
This video will give you a general introduction to hashing. <br> | |||
<html> | <html> | ||
<iframe width="560" height="315" src="https://www.youtube.com/embed/2BldESGZKB8" frameborder="0" allow="accelerometer; autoplay; encrypted-media; gyroscope; picture-in-picture" allowfullscreen></iframe> | <iframe width="560" height="315" src="https://www.youtube.com/embed/2BldESGZKB8" frameborder="0" allow="accelerometer; autoplay; encrypted-media; gyroscope; picture-in-picture" allowfullscreen></iframe> | ||
</html> | </html> | ||
The video below helps us understand hashing within the context of [[Blockchain|blockchain]].<br> | |||
<html> | <html> | ||
<iframe width="560" height="315" src="https://www.youtube.com/embed/IGSB9zoSx70" frameborder="0" allow="accelerometer; autoplay; encrypted-media; gyroscope; picture-in-picture" allowfullscreen></iframe> | <iframe width="560" height="315" src="https://www.youtube.com/embed/IGSB9zoSx70" frameborder="0" allow="accelerometer; autoplay; encrypted-media; gyroscope; picture-in-picture" allowfullscreen></iframe> | ||
Latest revision as of 07:12, 18 March 2024
A hash function is any function that can be used to map data of arbitrary size to fixed-size values. The values returned by a hash function are called hash values, hash codes, digests, or simply hashes. The values are used to index a fixed-size table called a hash table. Use of a hash function to index a hash table is called hashing or scatter storage addressing.[2]
Hashing is the transformation of a string of characters into a usually shorter fixed-length value or key that represents the original string. Hashing is used to index and retrieve items in a database because it is faster to find the item using the shorter hashed key than to find it using the original value. It is also used in many encryption algorithms.[3]
Benefit of hashing[edit]
One main use of hashing is to compare two files for equality. Without opening two document files to compare them word-for-word, the calculated hash values of these files will allow the owner to know immediately if they are different.
Hashing is also used to verify the integrity of a file after it has been transferred from one place to another, typically in a file backup program. To ensure the transferred file is not corrupted, a user can compare the hash value of both files. If they are the same, then the transferred file is an identical copy.
In some situations, an encrypted file may be designed to never change the file size nor the last modification date and time (for example, virtual drive container files). In such cases, it would be impossible to tell at a glance if two similar files are different or not, but the hash values would easily tell these files apart if they are different.[4]
Simple Code sample[edit]
# this python file should be used as part of your process to understand hashing.
# please change values so you can see how hashing works!
import hashlib
string = "hello there."
print(string)
hashed_string = hashlib.sha256(string.encode()).hexdigest()
print(hashed_string)
# Thank you to Max S for coming up with this sample
Videos[edit]
This video will give you a general introduction to hashing.
The video below helps us understand hashing within the context of blockchain.