VPN: Difference between revisions
Mr. MacKenty (talk | contribs) No edit summary |
Mr. MacKenty (talk | contribs) |
||
| Line 6: | Line 6: | ||
I thank the Dartform Grammar School for this material<ref>http://ib.compscihub.net/wp-content/uploads/2015/04/3.1.4.pdf</ref> | I thank the Dartform Grammar School for this material<ref>http://ib.compscihub.net/wp-content/uploads/2015/04/3.1.4.pdf</ref> | ||
<br /> | <br /> | ||
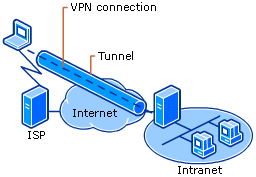
[[File:Vpn tunnel.gif]] | |||
* A LAN that is connected to the internet. | * A LAN that is connected to the internet. | ||
* One computer outside of the LAN that is also connected to the internet. | * One computer outside of the LAN that is also connected to the internet. | ||
Revision as of 13:14, 15 November 2017
Networks[1]
A virtual private network (VPN) extends a private network across a public network, and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. Applications running across the VPN may therefore benefit from the functionality, security, and management of the private network.[2]
Required technologies[edit]
I thank the Dartform Grammar School for this material[3]
- A LAN that is connected to the internet.
- One computer outside of the LAN that is also connected to the internet.
- VPN client and server running on the lone machine and the original LAN
- Internet connection
In addition, you also need to understand VPN requires:
- encryption (the process of encoding a message or information in such a way that only authorized parties can access it[4])
- tunneling (allows a network user to access or provide a network service that the underlying network does not support or provide directly[5])
A video explaining VPN basics[edit]
Evaluate the use of a VPN[edit]
A VPN allows telecommuting. Telecommunicating
A video describing some of the benefits of a VPN[edit]
Standards[edit]
These standards are used from the IB Computer Science Subject Guide[6]
- Identify the technologies required to provide a VPN.
- Evaluate the use of a VPN.
References[edit]
- ↑ http://www.flaticon.com/
- ↑ https://en.wikipedia.org/wiki/Virtual_private_network
- ↑ http://ib.compscihub.net/wp-content/uploads/2015/04/3.1.4.pdf
- ↑ https://en.wikipedia.org/wiki/Encryption
- ↑ https://en.wikipedia.org/wiki/Tunneling_protocol
- ↑ IB Diploma Programme Computer science guide (first examinations 2014). Cardiff, Wales, United Kingdom: International Baccalaureate Organization. January 2012.